The Key to
Data Security
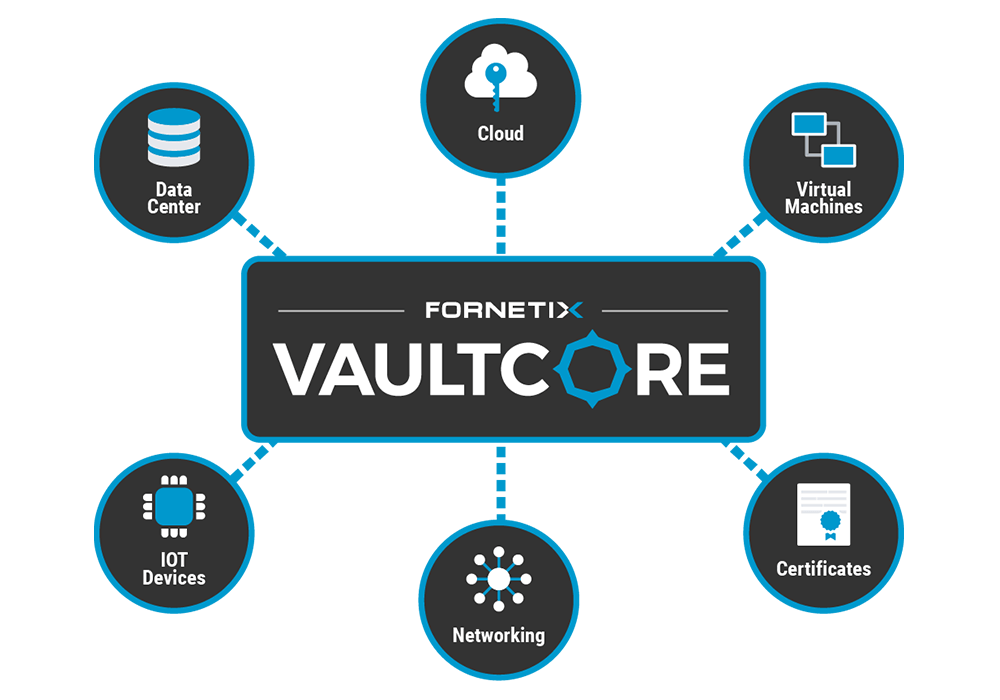
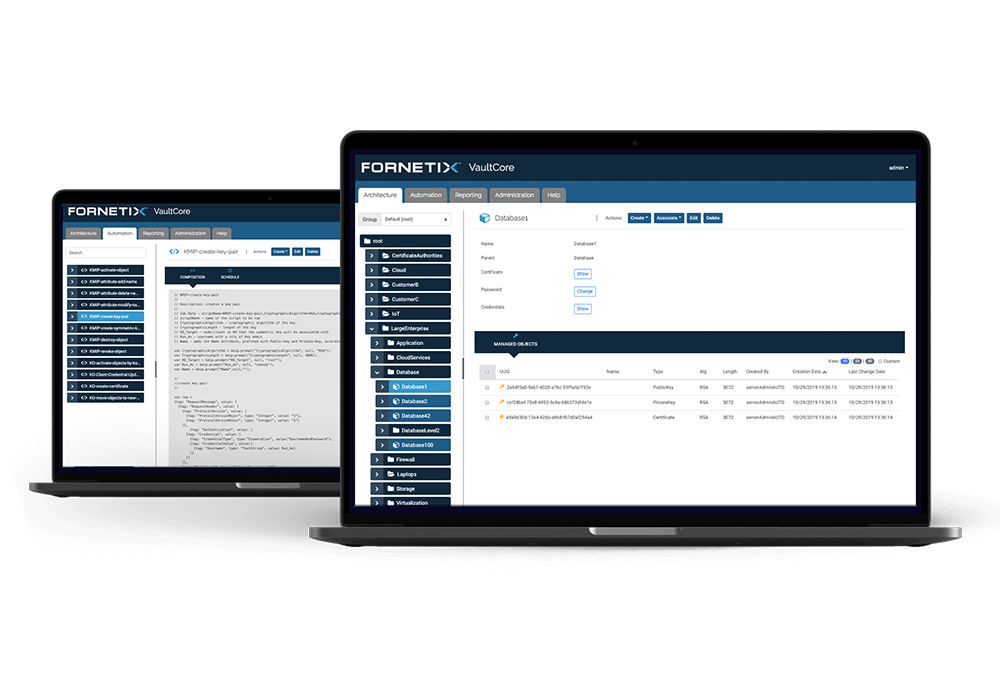
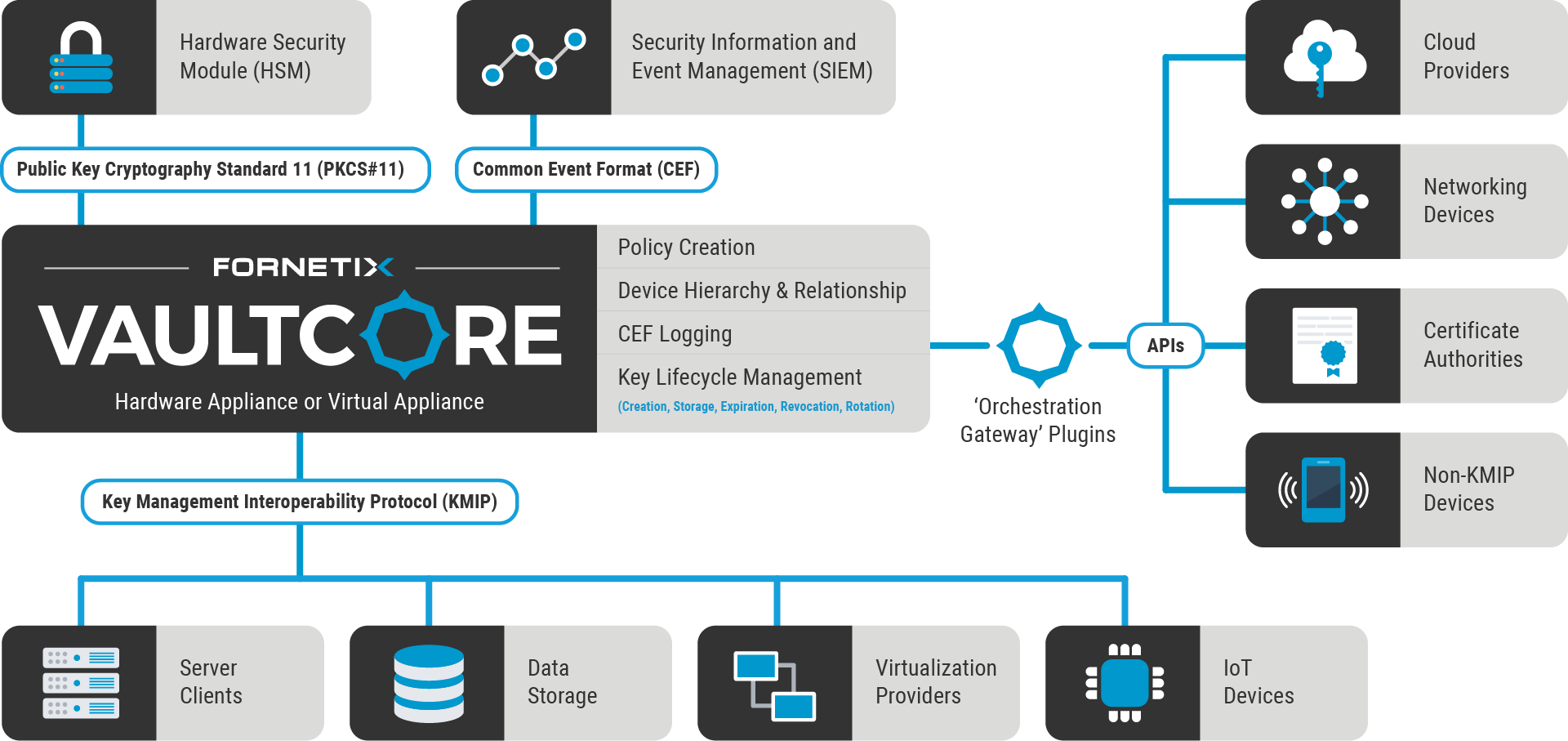
VaultCore® was built to make encryption of data seamless, rapid, flexible, scalable, and budget friendly. We connect with leading technologies around the globe to automate and orchestrate key management and encryption on a massive scale. Simple, centralized control of security and access policies prevent human error, reduce operating costs, safeguard critical data, and ensure regulatory compliance.